I bought myself a Yubikey 5 NFC1, I am planning to integrate it into my next piece of software. In order to do so, I will need to set it up first. I will try to describe it here so I can keep it for my future reference, but also to ease the start for others. Now I am on an Intel Mac running the latest MacOS Ventura, therefore this will be most applicable on similar systems. Throughout this article I will be using asciinema to visualize some actions in the terminal. Nice about it is that you are able to copy and paste from it to your own terminal, if you desire.
What I would like to achieve ultimately with this key and probably a second key later on is the following:
- Store gpg keys
- Store some x509 certificate
- Use it with an email tool on macOS, to send encrypted mails
- Use it with an email tool on iOS
Generally I am not sure what I can achieve with this nifty piece of tech, but I am gonna find out. Just to ensure total key integrity and no loss I will use this one for testing purpose only and later on purchase an additional key for “production” purpose.
Lets Go
When browsing to yubico.com to see how to get started, I realized that I had to scroll nearly all the way to the bottom. This could have been done better. For you, if you do not want to scroll all the way down and click yourself through, use this link to download the yubikey-manager.
Initialization
OK, Yubikey Manager is installed, I launched the application and plugged the key. I am pleasantly surprised by the LED under the Y, seems the key is alive. Interesting is that the Key Manager gives me full control over the interfaces. See the screenshot below. I didn’t expect this but I think its a really nice feature.
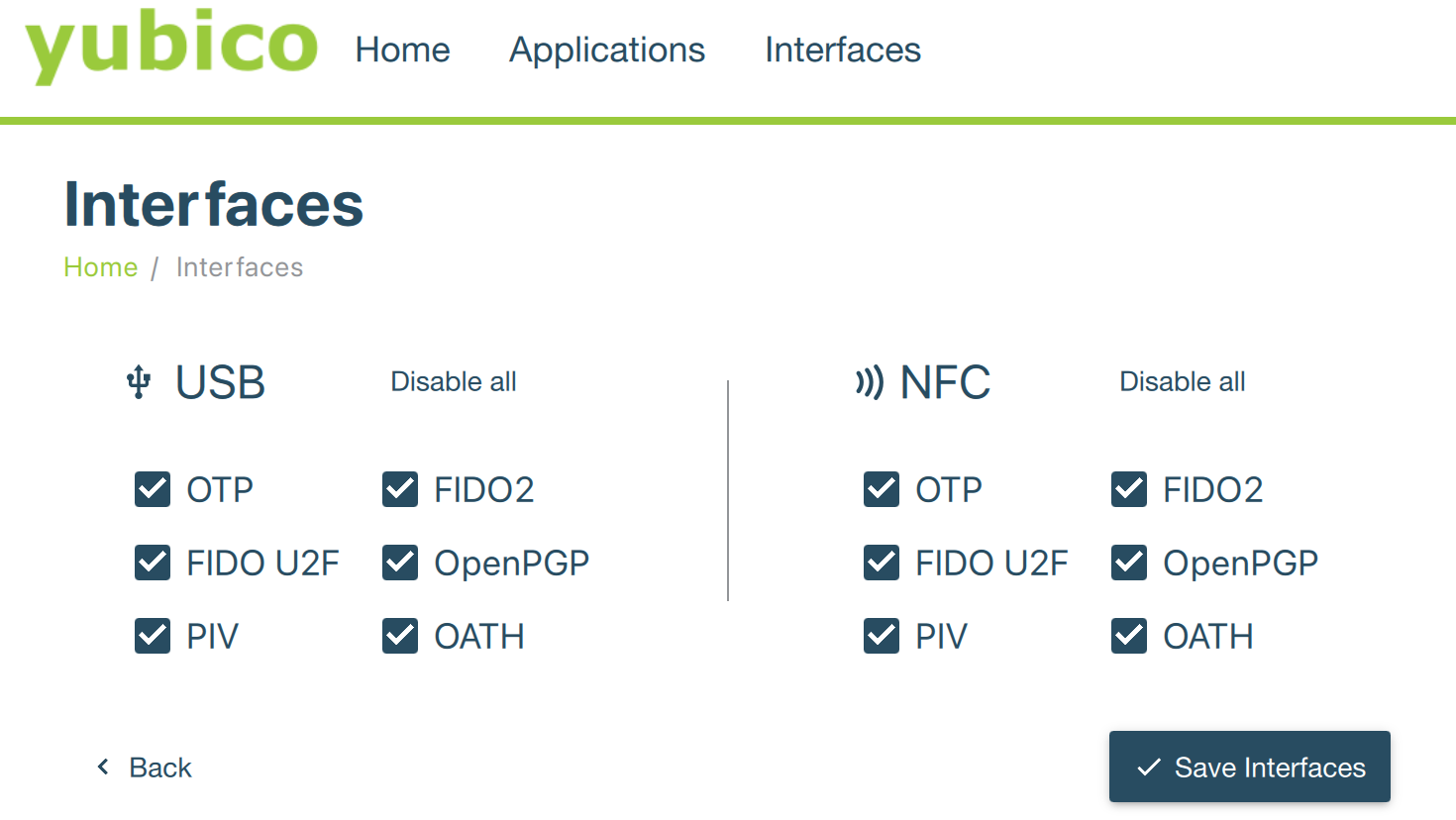
Lets start the setup of the key. First we will need to reset the admin pin and the access pin. The default value for the admin pin is: 12345678 While the default value for the access pin is: 123456
See how to reset your pin and admin pin in the asciicast2 below.
Pin reset
Now it is time to generate a pgp key. As I already stated earlier this is for non prod, which is why I am doing this on my current system. For a production grade key, you should generate it in a Linux Live image, or directly on the key. However, if you opt for on chip key generation, do not forget, that you will not be able to backup your key.
Key generation
We will start with the Encryption key generation. This RSA key will be valid for 10 days, and have a key length of 4096bits
Script everything
Factory Reset
#Factory reset gpg-card just too ensure we are really at a init level
gpg-card factory-reset
#When prompted answer y and yes
Reset PINs
#Reset the admin pin, the access pin and the reset code
gpg-card
passwd
Generate keys
#Reset the admin pin, the access pin and the reset code
gpg --expert --full-gen-key
# For best compatibility you might want to go with RSA 2048
# If it makes sense to you, use ECC (9)
# I will choose the default Curve 25519 to gain support for EdDSA (1)
# Please select what kind of key you want:
# (1) RSA and RSA
# (2) DSA and Elgamal
# (3) DSA (sign only)
# (4) RSA (sign only)
# (7) DSA (set your own capabilities)
# (8) RSA (set your own capabilities)
# (9) ECC (sign and encrypt) *default*
# (10) ECC (sign only)
# (11) ECC (set your own capabilities)
# (13) Existing key
# (14) Existing key from card
# Your selection? 9
# Please select which elliptic curve you want:
# (1) Curve 25519 *default*
# (2) Curve 448
# (3) NIST P-256
# (4) NIST P-384
# (5) NIST P-521
# (6) Brainpool P-256
# (7) Brainpool P-384
# (8) Brainpool P-512
# (9) secp256k1
# Your selection? 1
# Please specify how long the key should be valid.
# 0 = key does not expire
# <n> = key expires in n days
# <n>w = key expires in n weeks
# <n>m = key expires in n months
# <n>y = key expires in n years
# Key is valid for? (0) 0
# Key does not expire at all
# Is this correct? (y/N) y
# generate sub keys with gpg --expert --edit-key #KEYID
Copy Key to YubiKey
gpg --expert --edit-key #KEYID
#select the key you like
key KEY123
keytocard
#Select the correct slot 1 for Signature, 2 for encryption and 3 for authentication
Takeaways
The most secure storage for your key is your Yubikey. You can generate your keys directly on the device. You will however not be able to back your key up.
It is recommended to have a spare key. You initialize booth the same way, so that in case you lose/break one you still have a standby.
You should upload your key to a keyserver if you want to publicize it the easy way. One popular server is hosted by ubuntu.
gpg --send-keys --keyserver keyserver.ubuntu.com 123ABC